6 Tricks to Torrent secure | Torrent safely with a VPN & more-MyCyberBase
 [ad_1]
[ad_1]
Torrenting may also be a particularly dangerous trade. No longer solely are you able to stumble throughout motion pictures, TV presentations, and packages that grow to be stuffed with viruses and malware, however you should finally end up in criminal hassle because of copyright restrictions. Alternatively, through following along side the six guidelines on this information, you are able to torrent safely.
Caution:
ProPrivacy neither condones nor encourages the torrenting of any copyrighted subject matter. Torrenting such fabrics is unlawful in maximum, if no longer all, international locations and may just result in each prison and civil prosecution.
What are the dangers of torrenting?
Grabbing pirated content material from BitTorrent can prevent some huge cash, however you'll be able to want to remember that it is unlawful to obtain copyrighted subject matter similar to track, films or video games. You want to be served a stop and desist letter through your Web Provider Supplier (ISP), must pay a high-quality to the copyright holder, and even finally end up in courtroom on prison fees.
Widespread presentations like Squid Sport, South Park, and Sport of Thrones are malware hotspots, too. Hackers know those collection can be downloaded tens of millions instances, making them a very simple technique to infect folks with malware, spyware and adware, trojans and different malicious systems that may take your gadget and data hostage. At one level, Sport of Thrones chalked up essentially the most inflamed torrents – with 30,000 inflamed torrents found out through Kaspersky Labs.
Tips on how to keep secure when torrenting
The dangers posed through torrenting are actual and probably severe, however there are methods to mitigate them. Beneath, we now have indexed our most sensible guidelines for staying secure when torrenting, and you'll navigate thru them through clicking the hyperlinks beneath:
Use a VPN for more secure torrenting
The use of a VPN for torrenting is a no brainer. A VPN encrypts your entire incoming and outgoing knowledge, which in flip prevents your ISP from monitoring the internet sites you discuss with. So, they will do not know if you are downloading one thing from a torrent repository! With a VPN, you'll be able to have advanced virtual privateness, that means that you'll be able to be unfastened to surf with out concern of repercussions.
VPNs additionally save you the internet sites and products and services you discuss with from monitoring your actual IP cope with. Because of this, any individual making an attempt to watch people downloading torrents will be unable to get their arms in your IP cope with – they will simply see the IP cope with belonging to the VPN server, as an alternative.
Admittedly, there's a centered means that can be utilized to trace down VPN customers. That is referred to as a time correlation assault, which is thankfully smooth to keep away from in case you keep on with zero-log VPN suppliers. Those suppliers are regarded as the cream of the crop inside the privateness neighborhood, and they are why we propose that avid torrenters keep on with VPNs that provide this assurance.
Concealing your IP cope with additionally has safety advantages. When torrenting by the use of peer-to-peer, you might be probably promoting your house’s IP cope with to everyone else who is attached to the peer. If anyone on that peer is a hacker, they may probe your IP cope with for open ports or for IoT units so as to add to a botnet. The use of a VPN guarantees that fellow torrenters at the peer can’t unmarried you out.
If you wish to be informed extra about how a VPN can assist, see our what's a VPN information.
Can I exploit any VPN supplier?
No longer each VPN lets in torrenting, seeing as it is resource-heavy and will vastly have an effect on the price of operating their VPN servers.
The extra knowledge that is downloaded, the extra knowledge should be processed, and the server farms that VPN suppliers hire from can finally end up charging them extra for the excitement.
As well as, torrent downloads fritter away a large number of bandwidth which is able to additional decelerate VPN servers. This in the long run reduces total efficiency and places a pressure at the VPN community – which is unhealthy information for different customers, who may come upon lag and slow speeds when connecting to a server.
Alternatively, the VPNs that do allow torrenting most often stay 0 logs, in order that none in their subscribers can ever be singled out. They will additionally run their provider on an enormous community of Tier-1 servers able to dealing with large quantities of information at lightning-fast speeds.
And the perfect VPNs put aside explicit servers for torrenting! Those use load balancing to make certain that customers are routinely hooked up to much less congested servers, which is helping the VPN care for a easy provider for all of its subscribers.
Which VPN must I exploit for torrenting?
There is a lot that must be regarded as when deciding which VPN to make use of when torrenting. To assist, we've got compiled an inventory of our favorite torrent-friendly VPNs, the place we additionally duvet the primary concerns you wish to have to make prior to committing to at least one.
The most efficient torrenting VPNs
Take a look at you’re the use of the precise seed
Fending off malware and different exploits is a number one worry for many torrenters. The excellent news is that there are a number of techniques of recognizing and staying clear of malicious seeds.
Were given seeds?
The best way to be sure you're if truth be told downloading what you are searching for is to seek for common torrents. If a torrent has a large number of seeders, it is most probably the actual deal.
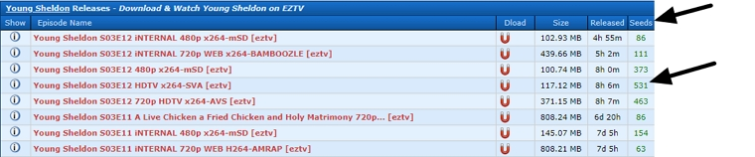
Upload just a little aptitude
The use of common torrent repositories like EZTV or YTS is a smart (and secure) technique to to find what you are after. Most of these websites use 'aptitude' methods to spotlight verified customers – which makes it even more straightforward to determine whether or not a seed is authentic or no longer.
On ThePirateBay, as an example, moderators spotlight customers who continuously add content material that is freed from malware through giving them a Relied on tag. The VIP tag is the same, however is there to indicate a seeder who is very devoted.

The ‘Relied on’ tag is a crimson cranium and the ‘VIP’ tag is a inexperienced cranium. Alternatively, the ‘aptitude’ will glance other relying at the web site that you just use. Be certain that to do a little analysis and be informed what’s what to search out highlighted customers at the website online you propose to make use of!
Torrent websites permit customers to depart feedback, and checking them is every other fast method to determine whether or not a seed is malevolent. Just right-quality torrents are most often praised through different downloaders, too, so it briefly turns into clean which of them are value your time.
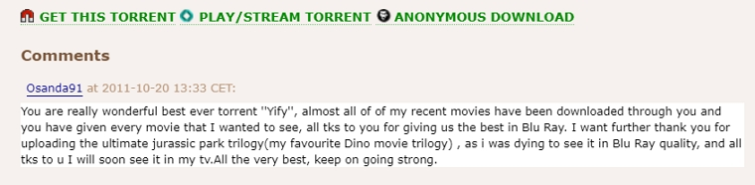
To search out the feedback, get started through looking for the content material you are after. Subsequent, click on at the torrent seed that takes your fancy, and scroll all the way down to learn what persons are pronouncing!
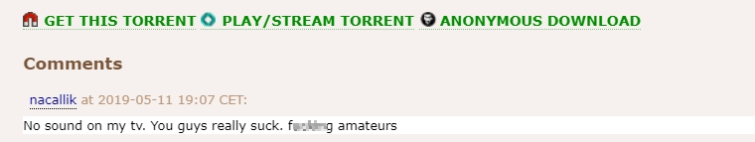
After all, all the time take into account to be in search of trolls, who might both overly reward a garbage seed or criticize a sound seed with out a authentic explanation why.
Set up a excellent antivirus
Having dependable antivirus instrument is simply excellent observe when browsing the internet. Hackers like to cover malware within torrent downloads, simply infecting the customers who obtain them. Cybercriminals remember that hiding malware in a torrent report can let them infect large numbers of folks, and that is with regards to one of the simplest ways to power exploits onto sufferers.
Ransomware, Trojans and different nasties
Being stuck through an exploit can permit hackers to take keep watch over of your instrument. Ransomware infections permit the attacker to take your gadget hostage, encrypting it till you pay them in Bitcoin.
Trojans, however, let the hacker commandeer your instrument’s microphone or digital camera to listen in on you, thieve the information to your telephone, set up keyloggers to thieve your passwords and monetary knowledge, and thieve your whole recordsdata, footage, and contacts.
Trojans are incessantly downloaded through unwitting folks torrenting pc systems, because the person is making an attempt to obtain an executable (.exe) report. On this structure, it is smooth to switch out the predicted program with an endemic, making the possible ramifications of downloading from torrent websites reasonably frightening.
Does my report dimension glance giant on this?
Fending off .exe and .bat recordsdata solely is hard, even though it's endorsed to persuade clean from them the place imaginable. Thankfully, you'll generally spot pretend installers through checking the scale of the obtain towards the scale of the real installer. Ideally it must be an identical, however there may also be some variances relying at the model or add. If the adaptation is noticeable, then again, it is a signal that the report might not be what you sought after.
Remember
Checking report sizes isn't a foolproof means of recognizing an inflamed torrent report. Hackers are getting smarter through the day. For general coverage you wish to have a excellent and up-to-the-minute antivirus and anti-malware program. To assist, we've got indexed some really useful antivirus programmes that you'll use when torrenting.
To find the most productive antivirus
Obtain to a sandbox atmosphere
That is an increased safety precaution that the general public will most probably no longer want to take. Alternatively, in case you incessantly obtain executable recordsdata (pc systems) from torrent repositories, then it is a good suggestion to offer protection to your self on this method.
Your sandbox, your laws!
Downloading recordsdata to a sandboxed atmosphere guarantees that malicious recordsdata is not going to infect your whole gadget in case you by chance obtain an endemic or malware. You'll then take a look at the report is legitimate prior to putting in it onto your primary gadget. Sandboxie is a useful gizmo that lets you create a sandboxed atmosphere in your PC.

Then again, it's possible you'll favor to put in a complete Digital Gadget (the use of Parallels or VirtualBox, as an example) and take a look at the report there first. To take action, merely obtain the torrent onto your VM, use VirusTotal to scan the report, and if VirusTotal provides it the all-clear, then run the report within the VM to verify it's good enough. If the report is blank, and the installer works high-quality within the VM, you might be high-quality to transport this system over onto your actual working gadget.
Non-public trackers are closed-door torrenting communities designed to keep the standard of torrents. While you sign up for any such communities, you'll be able to be amazed on the high quality of torrents seeing as each and every is punctiliously hand-picked the use of a strict moderation procedure.
Non-public trackers are most often invitation-only – and issues get much more irritating while you believe that those communities also are incessantly one-in-one-out. Because of this, present participants guard their spot jealously and seldom hand over the neighborhood.
These days, there are a number of well known personal torrenting communities which can be extremely sought-after. Those come with PassThePopcorn, IPTorrents, Demonoid, and Zeronet.
When you do arrange to get a call for participation to any such golf equipment, you'll be able to be in an atmosphere the place you'll agree with the standard of the torrents. This may occasionally make you some distance much less more likely to come throughout malicious recordsdata, viruses, malware, unsolicited mail, and Trojans.
How do you get into any such sought-after torrenting golf equipment?
One choice is to hang around on common torrent forums like /r/torrent on Reddit. Spending time on this sort of board and making pals with different customers may just in the end get you a call for participation. Alternatively, it is important to be an energetic member of the neighborhood and construct agree with through the years, reasonably than just flip up and get started not easy a call for participation.
It is all about that ratio
It's value making an allowance for that if you do arrange to sign up for a closed-door neighborhood, there can be sure laws. Maximum of them require you to care for an up/down ratio, so it is important to add knowledge in addition to obtain it, serving to different participants of the neighborhood through seeding the downloads they would like.
Maximum communities call for that you just care for no less than a 1:1 ratio, which is the place you obtain the same quantity as you add. Admittedly, while you sign up for a brand new neighborhood, it may be exhausting to control this in an instant. The excellent news is that each one new customers are given a grace duration to succeed in this equilibrium.
While you do type out your ratio, you are going to be some distance much less more likely to get booted from the neighborhood. So, if you're failing to type out your ratio, it's possible you'll wish to believe giving a donation to the neighborhood (for the price of servers, and so on). Alternatively, keeping up a excellent ratio is best, and can even acquire you perks similar to VIP standing and an upgraded account at the tracker with quicker obtain speeds.
Tips on how to enhance your ratio
To you'll want to reach the golden ratio, get started out through downloading some smaller recordsdata that you just imagine could also be common. After you have those recordsdata, different individuals who wish to obtain them would require you to add it to them – which can set you in your method!
To the similar ends, this can be a excellent thought to obtain newly launched torrents briefly; if you're one of the crucial first to obtain, you might be much more likely to have luck in seeding them again to different neighborhood participants. Additionally, make sure you steer clear of 0 leech torrents, you need common recordsdata that folks wish to obtain; as this may increasingly let you to succeed in your 1:1 ratio.
Conclusion
Torrenting is huge possibility, giant praise – however there are methods to reduce the ones dangers. Search out energetic (and respected) torrenting communities, you'll want to're downloading the precise seeds, and put money into a VPN if you are excited about safeguarding your safety.
And, if you wish to have a last reminder of the VPNs we propose for torrenting, then take a look at the desk beneath:

From $2.69/Month
The most efficient VPN for torrenting. An open supply provider with a confirmed no-logs coverage, and heaps of security measures. Features a 30-day money-back ensure.
- ProPrivacy TrustScore:
- 10 out of 10
- Simultaneous connections
- 10
- Server places
- 84
- Unfastened trial
- No

From $4.13/Month
The most efficient midrange VPN for torrenting. Customers get apps for all platforms and powerful encryption for a value that may not cost a fortune – and a 30-day money-back ensure.
- ProPrivacy TrustScore:
- 9.9 out of 10
- Server places
- 60
- Simultaneous connections
- 6
- Unfastened trial
- No

From $3.75/Month
The most efficient user-friendly VPN for torrenting. It has easy-to-use apps with a integrated kill-switch and leak coverage, in addition to a 30-day money-back ensure.
- ProPrivacy TrustScore:
- 9.8 out of 10
- Simultaneous connections
- Limitless
- Server places
- 75
- Unfastened trial
- No

From $6.67/Month
The most efficient feature-rich VPN for torrenting. A top rate provider with tough encryption and an audited zero-logs coverage, and a complete raft of options. Features a 30-day money-back ensure.
- ProPrivacy TrustScore:
- 9.7 out of 10
- Simultaneous connections
- 5
- Unfastened trial
- No
- Server places
- 160

From $2.30/Month
The most efficient worth VPN for torrenting. Customers get limitless simultaneous connections and apps for all platforms, permitting flexible torrenting. Additionally gives a 30-day money-back ensure.
- ProPrivacy TrustScore:
- 9.6 out of 10
- Simultaneous connections
- Limitless
- Unfastened trial
- Sure
- Server places
- 108
Comments
Post a Comment